PS it’s not our thumbs, it’s their thumbs
Whoopsie, it seems the brave rebels who stormed their own Congress have realized they’re getting themselves in trouble. Caroline Orr @RVAWonk:
They’re all realizing that live-tweeting from inside SCIF is a huge security breach and now they’re trying to tweet their way out of it.
It’s staff tweeting! We’re not tweeting!
Oh look, another one:
I’m not quite sure it becomes not a security breach if they send it to staff who then send it to the world. I kind of think it’s the whole sending it thing that’s the breach. Could be wrong.
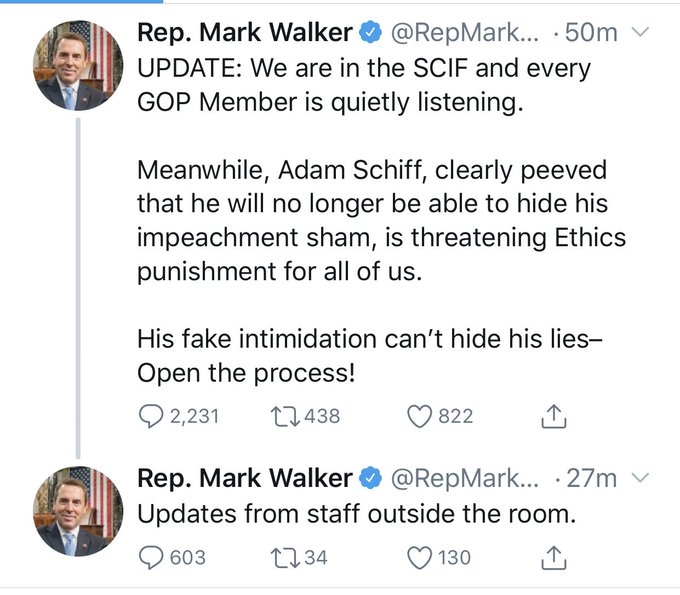
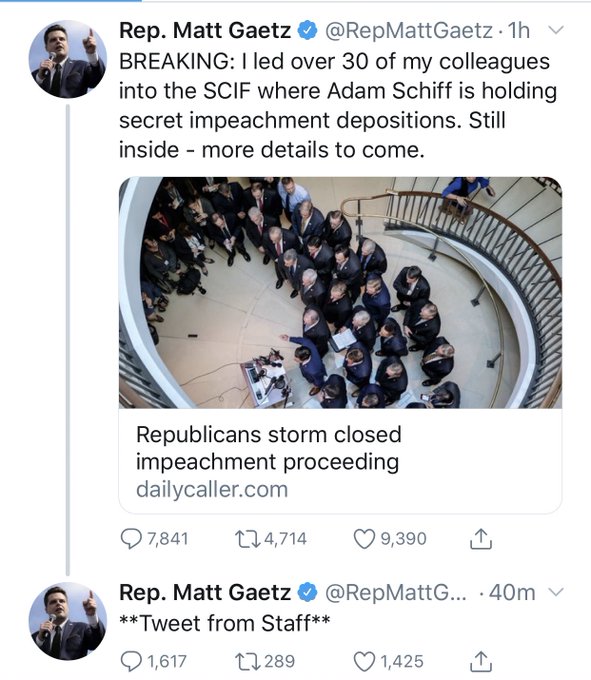

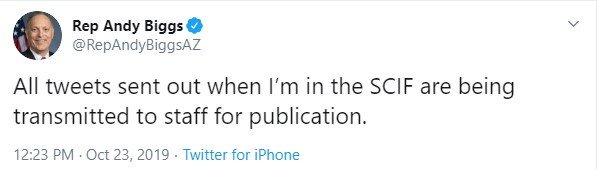

Yeah, how were they communicating with the staff outside the secure area? Totally going to fly.
I think there’s two issues.
One issue is if they are disclosing confidential information they are learning in the hearing room. As far as I know, that hasn’t been the case — the deposition didn’t begin until after this stunt was basically done, and the tweets are basically just about how mad Adam Schiff is and how brave the GOP members are, etc. I suppose there might be some blanket rule that “anything that happens in a SCIF is automatically confidential,” but I don’t think so, or else we wouldn’t have heard the details of Taylor’s testimony yesterday.
The other issue is that apparently bringing any kind of electronic device into a SCIF is forbidden. Cell phones in particular are easily corrupted by malware and can be turned into listening devices. Members and others are required to lock up their devices in little boxes outside the SCIF before entering. What’s worse is that, according to some security experts I’ve been reading today, once a phone has been brought into a SCIF, it isn’t sufficient to just remove the phone. For technical reasons the experts were unable to disclose because they related to security countermeasures, there are additional steps that have to be taken to “re-secure” the SCIF again. (I’m speculating here, but perhaps the concern is that a compromised phone could transmit malware to the hardware inside the SCIF that creates a back door or otherwise compromises it, so they have to run the top security equivalent of a malware scan to be sure.)
As to Issue #2, if the members are still in possession of their phones inside the SCIF, then they’re compromising security whether they are sending Tweets directly to Twitter, or texting/DMing their staff things to tweet, or even just sitting there in possession of a smartphone. On the other hand, if they are stepping out of the room to hand physical notes to staff to be tweeted from outside, that would presumably be ok.
My post crossed with Chris T’s, so I’ll just add: the sudden “uh, this was tweeted by staff” follow-ups look pretty dubious given the timing.
For more info on SCIF procedures, here is the Twitter thread that What a Maroon linked to another post.
@Chris Semaphore, obviously. :-D
Thanks for that thread, Screechy and What a Maroon.
https://threadreaderapp.com/thread/1187032800572125191.html
@Claire: maybe tapping code? A whole hallway full of aides with a phone in one hand and and a glass pressed against the wall?
The sad thing is that this doesn’t even seem that strange anymore. We can’t even see the Overton window from where we stand.
I’m sure they used carrier pigeons.
Messages in a bottle? I guess that would only work if the building was flooded.
I assume that the references to Schiff’s ‘dungeon’ and ‘secret chamber’ are intended to create some kind of link in the minds of the GOP faithful to Hillary and Obama’s secret ‘pizza shop sex dungeon’.
I suppose. I hadn’t thought of that. I thought it was meant to bring up ideas of the Inquisition and witch hunting.